Why Ethical?
Today, I am going to talk about an introduction to a subject that I learn in my university, I am a computer student and currently learning some computer subjects including this subject called “Ethical Hacking”. If you as a student take computer forensics and security as the study program / stream, then only you can enroll this subject, not really sure maybe there are one or two more study program related to the subject. So, lets talk about the subject.
Basically we all know what hacking does, which can be described with words such as “break in” and it is a job to illegally access through a network security which means hacking is gaining access without any permission from the network’s owner. Moreover, other than just gaining access and also accessing into it, hackers can also get the file that he / she wants or you can say, stealing, because you get the file without permission and or even delete it from the original location. Hacking is a cyber crime, you can get penalized by doing it because it is also counted as criminal job and close to a thief in real life. In my university, they want us, the computer students, to solidly understand the concept of hacking and use it for a good and better purpose, so they named the subject with “Ethical” in front of the word “Hacking”.
There are of course, difference between hacking ethically and simply just hacking… Small differences, but big consequences. Well, if you read “Ethical” you will immediately understand something, a good way or a good manner and yes it is. Ethical hacking is hacking legally, on which you are an employee hired by a company to do penetration test and only allowed to do it to your own company’s network to detect or check weaknesses to prevent network being hacked by those cyber thief. Penetration testing is no different than hacking.. the only thing is, simply pentest is only to test the network’s protection. Giving reports and solutions to the owner is these tester’s job. Ethical hackers can be imagined as a police that prevent the thief to act or even caught them while they act. Law is the stuff that ethical hackers want to consider. Laws are slightly different on each every places, so it is best to read the law agreement each time you want to do something related to it. All of the above that i have wrote shows that ethical hacking is almost the opposite of the illegal hacking.
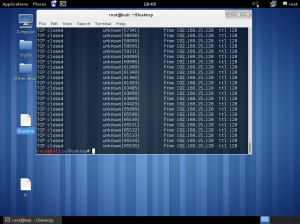
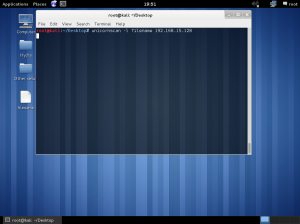
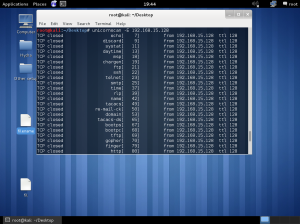
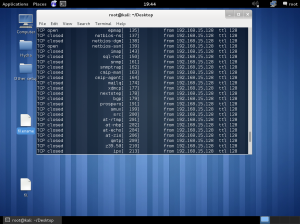
Lab work
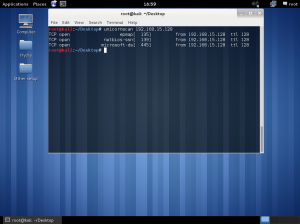
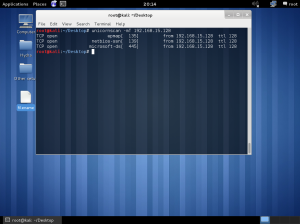
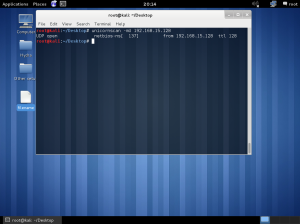
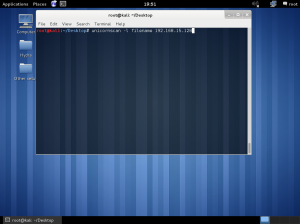
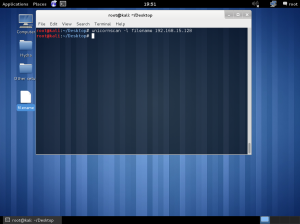
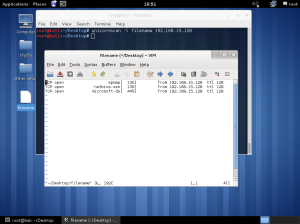
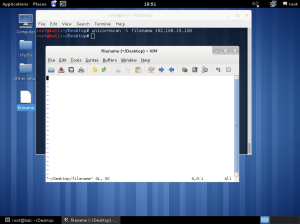
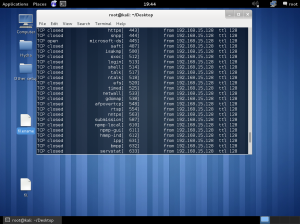
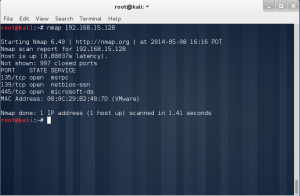
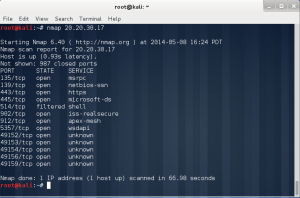
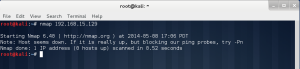
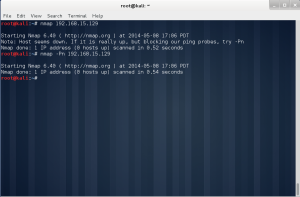
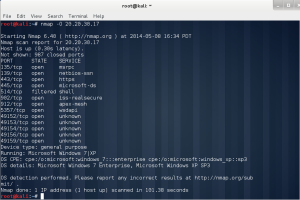
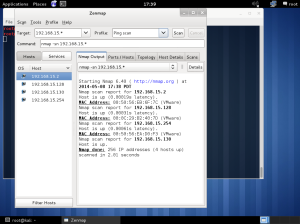
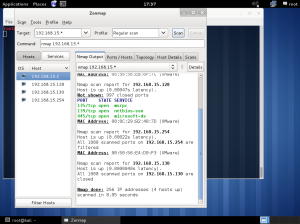
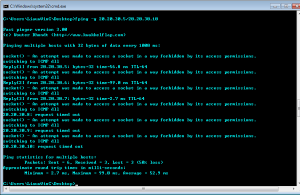
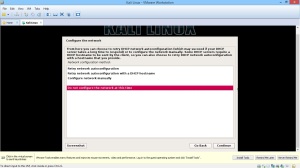
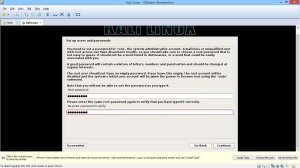
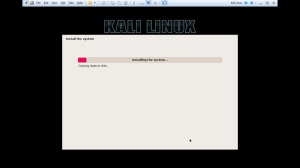
In the lab session, installed vmware, vm – virtual machine.
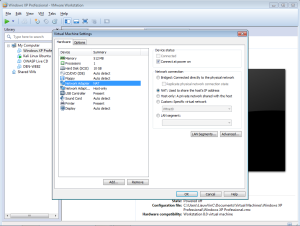
In the vmware, you can create a new virtual machine by clicking the blue marked square.
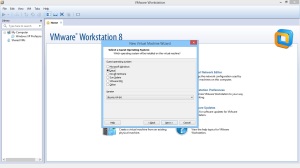
Os – win xp
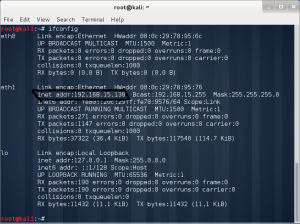
Enable internet through right click and then to setting
Need this nat adapter like this one
To do that, go click the button “Add” below those and choose “Network adapter”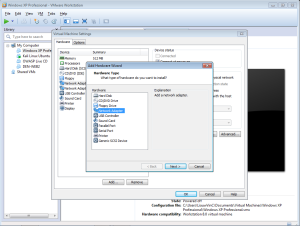
And choose “Nat”
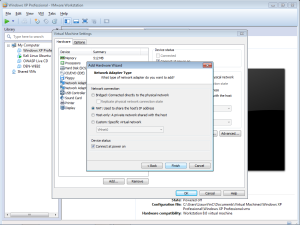
Disable the windows firewall if needed, and.. internet connected.